re:Invent2013にて、CloudTrailの発表があったので触ってみました。
CloudTrailは、AWSのAPIコールの記録をS3にログとして保存するサービスです。
これによってセキュリティ分析や運用チェックなどを行うことが可能です。
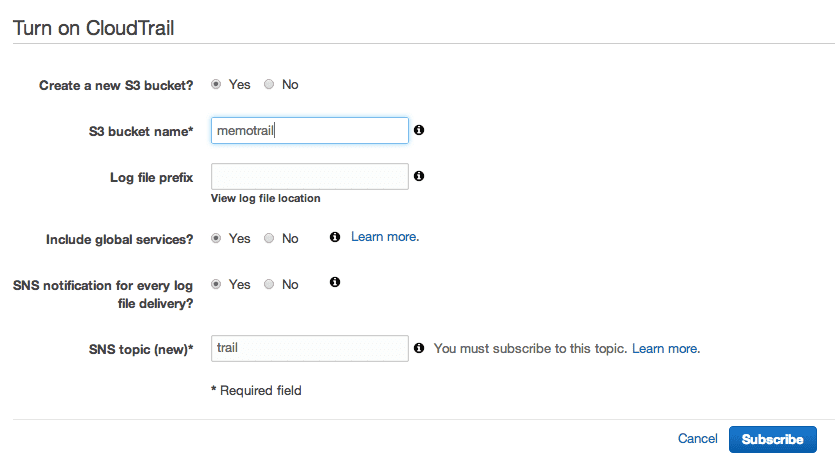
AWSコンソールをみるとCoudTrailが追加されているので、開いてみます。

ログの保存先のS3バケットを指定して、必要であればその他のオプションも設定します。
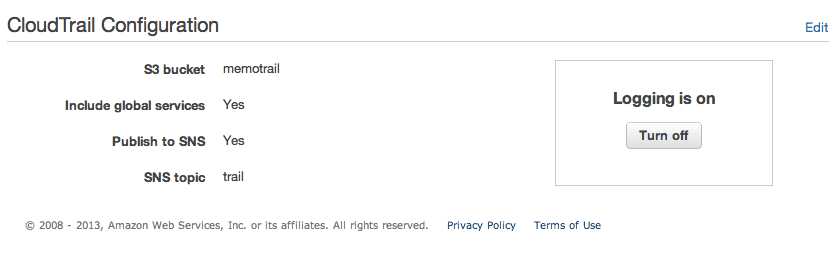
しばらく、AWSの操作をしたあと、出力先に設定したS3バケットを確認します。
すると、以下のようにjson形式のログファイルが圧縮された状態で日ごとに保存されるようになります。
{
"Records": [
{
"awsRegion": "us-east-1",
"eventName": "DescribeRouteTables",
"eventSource": "ec2.amazonaws.com",
"eventTime": "2013-11-15T18:08:00Z",
"eventVersion": "1.0",
"requestParameters": {
"filterSet": {},
"routeTableIdSet": {}
},
"responseElements": "",
"sourceIPAddress": "54.249.240.229",
"userAgent": "aws-sdk-php/1.6.2 PHP/5.4.20 curl/7.19.7 openssl/1.0.0-fips",
"userIdentity": {
"accessKeyId": "xxxxxxxxxxxxxxxxxx",
"accountId": "821635308497",
"arn": "arn:aws:iam::821635308497:root",
"principalId": "821635308497",
"type": "Root"
}
},
{
"awsRegion": "us-east-1",
"eventName": "DescribeSubnets",
"eventSource": "ec2.amazonaws.com",
"eventTime": "2013-11-15T18:07:59Z",
"eventVersion": "1.0",
"requestParameters": {
"filterSet": {},
"subnetSet": {}
},
"responseElements": "",
"sourceIPAddress": "54.249.240.229",
"userAgent": "aws-sdk-php/1.6.2 PHP/5.4.20 curl/7.19.7 openssl/1.0.0-fips",
"userIdentity": {
"accessKeyId": "xxxxxxxxxxxxxxxxxx",
"accountId": "821635308497",
"arn": "arn:aws:iam::821635308497:root",
"principalId": "821635308497",
"type": "Root"
}
},
{
"awsRegion": "us-east-1",
"eventName": "DescribeVpcs",
"eventSource": "ec2.amazonaws.com",
"eventTime": "2013-11-15T18:07:58Z",
"eventVersion": "1.0",
"requestParameters": {
"filterSet": {},
"vpcSet": {}
},
"responseElements": "",
"sourceIPAddress": "54.249.240.229",
"userAgent": "aws-sdk-php/1.6.2 PHP/5.4.20 curl/7.19.7 openssl/1.0.0-fips",
"userIdentity": {
"accessKeyId": "xxxxxxxxxxxxxxxxxx",
"accountId": "821635308497",
"arn": "arn:aws:iam::821635308497:root",
"principalId": "821635308497",
"type": "Root"
}
},
{
"awsRegion": "us-east-1",
"eventName": "DescribeSecurityGroups",
"eventSource": "ec2.amazonaws.com",
"eventTime": "2013-11-15T18:08:03Z",
"eventVersion": "1.0",
"requestParameters": {
"filterSet": {},
"securityGroupIdSet": {},
"securityGroupSet": {}
},
"responseElements": "",
"sourceIPAddress": "54.249.240.229",
"userAgent": "aws-sdk-php/1.6.2 PHP/5.4.20 curl/7.19.7 openssl/1.0.0-fips",
"userIdentity": {
"accessKeyId": "xxxxxxxxxxxxxxxxxx",
"accountId": "821635308497",
"arn": "arn:aws:iam::821635308497:root",
"principalId": "821635308497",
"type": "Root"
}
},
{
"awsRegion": "us-east-1",
"eventName": "DescribeNetworkAcls",
"eventSource": "ec2.amazonaws.com",
"eventTime": "2013-11-15T18:08:01Z",
"eventVersion": "1.0",
"requestParameters": {
"filterSet": {},
"networkAclIdSet": {}
},
"responseElements": "",
"sourceIPAddress": "54.249.240.229",
"userAgent": "aws-sdk-php/1.6.2 PHP/5.4.20 curl/7.19.7 openssl/1.0.0-fips",
"userIdentity": {
"accessKeyId": "xxxxxxxxxxxxxxxxxx",
"accountId": "821635308497",
"arn": "arn:aws:iam::821635308497:root",
"principalId": "821635308497",
"type": "Root"
}
},
{
"awsRegion": "us-east-1",
"eventName": "DescribeDBInstances",
"eventSource": "rds.amazonaws.com",
"eventTime": "2013-11-15T18:08:06Z",
"eventVersion": "1.0",
"requestParameters": null,
"responseElements": null,
"sourceIPAddress": "54.249.240.229",
"userAgent": "aws-sdk-php/1.6.2 PHP/5.4.20 curl/7.19.7 openssl/1.0.0-fips",
"userIdentity": {
"accessKeyId": "xxxxxxxxxxxxxxxxxx",
"accountId": "821635308497",
"arn": "arn:aws:iam::821635308497:root",
"principalId": "821635308497",
"type": "Root"
}
},
{
"awsRegion": "us-east-1",
"eventName": "DescribeVolumes",
"eventSource": "ec2.amazonaws.com",
"eventTime": "2013-11-15T18:08:04Z",
"eventVersion": "1.0",
"requestParameters": {
"filterSet": {},
"volumeSet": {}
},
"responseElements": "",
"sourceIPAddress": "54.249.240.229",
"userAgent": "aws-sdk-php/1.6.2 PHP/5.4.20 curl/7.19.7 openssl/1.0.0-fips",
"userIdentity": {
"accessKeyId": "xxxxxxxxxxxxxxxxxx",
"accountId": "821635308497",
"arn": "arn:aws:iam::821635308497:root",
"principalId": "821635308497",
"type": "Root"
}
},
{
"awsRegion": "us-east-1",
"eventName": "DescribeAddresses",
"eventSource": "ec2.amazonaws.com",
"eventTime": "2013-11-15T18:08:03Z",
"eventVersion": "1.0",
"requestParameters": {
"allocationIdsSet": {},
"filterSet": {},
"publicIpsSet": {}
},
"responseElements": "",
"sourceIPAddress": "54.249.240.229",
"userAgent": "aws-sdk-php/1.6.2 PHP/5.4.20 curl/7.19.7 openssl/1.0.0-fips",
"userIdentity": {
"accessKeyId": "xxxxxxxxxxxxxxxxxx",
"accountId": "821635308497",
"arn": "arn:aws:iam::821635308497:root",
"principalId": "821635308497",
"type": "Root"
}
},
{
"awsRegion": "us-east-1",
"eventName": "DescribeInstances",
"eventSource": "ec2.amazonaws.com",
"eventTime": "2013-11-15T18:08:02Z",
"eventVersion": "1.0",
"requestParameters": {
"filterSet": {},
"instancesSet": {}
},
"responseElements": "",
"sourceIPAddress": "54.249.240.229",
"userAgent": "aws-sdk-php/1.6.2 PHP/5.4.20 curl/7.19.7 openssl/1.0.0-fips",
"userIdentity": {
"accessKeyId": "xxxxxxxxxxxxxxxxxx",
"accountId": "821635308497",
"arn": "arn:aws:iam::821635308497:root",
"principalId": "821635308497",
"type": "Root"
}
}
]
}
このように呼び出したAPIの内容が表示されるため、jqやログ解析ツールなどと併用してAWSアカウントに対して
どういった操作があったかを簡潔に知ることが可能になります。
以上です。
こちらの記事はなかの人(memorycraft)監修のもと掲載しています。
元記事は、こちら